![]() The United States and Mexico are revving their engines for a joint venture into the world of semiconductors. On Thursday, the US State Department announced a new partnership to explore opportunities for strengthening the semiconductor supply chain in both nations. This collaboration comes at a crucial time, as the global demand for these tiny chips continues to soar.
The United States and Mexico are revving their engines for a joint venture into the world of semiconductors. On Thursday, the US State Department announced a new partnership to explore opportunities for strengthening the semiconductor supply chain in both nations. This collaboration comes at a crucial time, as the global demand for these tiny chips continues to soar.
The initiative stems from the US CHIPS Act, a 2022 legislation aimed at bolstering domestic semiconductor production and reducing reliance on foreign sources. Mexico, with its established manufacturing base and proximity to the US, presents a strategic partner for this endeavor.
The initial phase of the partnership will focus on assessing Mexico’s existing capabilities. This includes evaluating its current semiconductor industry, regulatory environment, and workforce readiness. This information will be key in determining the most effective ways for Mexico to contribute to a more resilient North American supply chain.
The potential benefits of this partnership are multifaceted. A stronger semiconductor industry in Mexico could create new jobs and economic growth. For the US, it translates to a more reliable source of chips, critical components in everything from smartphones to automobiles. Additionally, this collaboration strengthens the economic ties between the two nations.
While the road ahead may involve navigating technical and regulatory hurdles, the US-Mexico partnership presents a promising step towards a more secure and stable semiconductor supply chain for both countries. This cooperation could pave the way for a future where North America plays a more prominent role in this ever-important technological landscape.
Computer Repair in Louisville, KY: Keeping You Connected
The news about the US-Mexico partnership to strengthen the semiconductor supply chain is a great sign for the future of technology! Here at On-Site Louisville Computer Repair Co., we understand how important a reliable computer is – whether it’s for work, entertainment, or staying connected with loved ones.
Statistics show that the average computer user experiences a technical issue requiring repair at least once every two years. Common problems include slow performance, viruses, hardware malfunctions, and software crashes. These issues can be frustrating and disrupt your daily routine.
That’s where we come in! Our team of experienced technicians offers a wide range of computer repair services in Louisville, KY. We can diagnose and fix a variety of problems, from data recovery and virus removal to hardware upgrades and software installation. We work on desktops, laptops, and all major brands.
If you need computer repair in Louisville, KY, don’t hesitate to call On-Site Louisville Computer Repair Co. today! We’ll get your computer back up and running quickly and efficiently.
Category Archives: Computer Repair
Benefits of In-Home or On-Site Computer Repair and Service
 1. Convenience: One of the primary benefits is convenience. Customers don’t have to disconnect their computer systems and take them to a repair shop. Instead, technicians come directly to their location, saving time and effort.
1. Convenience: One of the primary benefits is convenience. Customers don’t have to disconnect their computer systems and take them to a repair shop. Instead, technicians come directly to their location, saving time and effort.
2. Personalized Service: In-home or on-site services offer a more personalized experience. Technicians can interact directly with customers, understand their specific needs, and provide tailored solutions accordingly.
3. Quick Turnaround Time: On-site services often result in faster turnaround times compared to off-site repairs. Technicians can diagnose and fix issues promptly, minimizing downtime for customers.
4. Hands-On Demonstration: In-home services allow technicians to provide hands-on demonstrations and tutorials to customers. This helps users learn how to prevent future problems and perform basic maintenance tasks.
5. No Risk of Damage During Transport: With on-site repairs, there’s no risk of damage during transport to a repair shop. This is particularly important for delicate equipment like desktops, monitors, and peripherals.
6. Minimal Disruption to Workflows: For small businesses, on-site repairs minimize disruptions to workflows. Employees can continue working while technicians resolve technical issues without interrupting operations.
7. Network and System Integration: Technicians can also assist with network setup, configuration, and troubleshooting on-site. This is beneficial for small businesses that rely on interconnected systems.
8. Transparent Pricing: In-home services often come with transparent pricing. Customers can get a clear understanding of the costs involved upfront, without hidden fees or surprises.
9. Builds Trust and Relationships: Providing on-site services helps build trust and long-term relationships with customers. They appreciate the convenience and personalized attention, leading to repeat business and referrals.
10. Customized Solutions: Technicians can offer customized solutions based on the customer’s environment and requirements. This ensures that the repairs or upgrades are tailored to meet specific needs.
How Long Does It Take to Repair Your Computer? The Time Frame Demystified
 In today’s digital age, where our lives are intertwined with technology, encountering PC issues is not uncommon. Whether it’s a slow computer, a tech support scam, hardware malfunction, software glitches, or something else – dealing with these problems can be frustrating. One of the burning questions many users have is: How long does it take to repair a PC? Let’s delve into this topic to understand the variables that influence repair times and what you can expect during the process.
In today’s digital age, where our lives are intertwined with technology, encountering PC issues is not uncommon. Whether it’s a slow computer, a tech support scam, hardware malfunction, software glitches, or something else – dealing with these problems can be frustrating. One of the burning questions many users have is: How long does it take to repair a PC? Let’s delve into this topic to understand the variables that influence repair times and what you can expect during the process.
Issue Complexity: The complexity of the problem plays a significant role in determining repair time. Minor issues like software conflicts or driver updates can often be resolved relatively quickly – if you find a fast computer repair company – usually within a few hours. However, more complex issues such as hardware failures or severe virus infections may require several days to diagnose and fix.
Diagnosis Phase: The initial phase of PC repair involves diagnosing the problem accurately. This step is crucial as an incorrect diagnosis can lead to ineffective solutions and wasted time. I always tell people that diagnostics might be the most important part of a repair. Depending on the issue’s nature, the diagnostic phase can take anywhere from a few minutes to several hours. Not all techs are created equal.
Repair Techniques: The methods used to repair your PC also impact the time frame. For software-related issues, technicians may employ tools to scan for malware, repair corrupted files, or reinstall operating systems. These tasks can be completed in minutes or be completed within a day or two depending on a variety of factors. On the other hand, hardware repairs such as replacing a faulty hard drive or upgrading components may take longer, especially if parts need to be ordered.
Availability of Resources: Availability of resources such as spare parts, software licenses, and skilled technicians can affect repair times. If a specific component needs to be replaced and it’s readily available, the repair process can be expedited. However, sourcing rare or specialized parts may cause delays.
Service Provider: The expertise and efficiency of the service provider also play a vital role. Reputable computer repair centers with experienced technicians often have streamlined processes that result in faster turnaround times. Conversely, choosing an inexperienced or unreliable service provider may lead to extended repair durations.
Communication and Updates: Transparent communication between you and the repair service is essential. A reliable service provider will keep you informed about the progress of your PC repair, any unexpected challenges encountered, and an estimated completion time. Regular updates can help manage expectations and reduce anxiety about repair delays.
Preventive Measures: In some cases, preventive measures may be recommended during the repair process to avoid future issues. This could include installing security software, updating drivers regularly, or implementing hardware upgrades. While these steps may add extra time to the repair process, they can enhance your PC’s overall performance and longevity.
Customer Cooperation: Your cooperation and responsiveness also contribute to timely repairs. Providing accurate information about the issue, promptly approving repair recommendations, and following any post-repair instructions can help expedite the process.
In conclusion, the time required to repair your PC can vary significantly based on factors such as the complexity of the issue, diagnosis accuracy, repair techniques, availability of resources, service provider efficiency, communication, preventive measures, and customer cooperation. While some repairs may be completed within hours, others could take several days or longer. Choosing a reputable and experienced repair service, staying informed, and actively participating in the repair process can help minimize downtime and ensure a successful outcome for your PC.
To Fix or to Ditch? Repairing vs. Replacing Your PC
 The blue screen of death. The grinding fan. The agonizingly slow startup. These are all signs your once-proud PC might be on its last legs. But before you toss it and shell out for a shiny new machine, consider this: repair versus replace.
The blue screen of death. The grinding fan. The agonizingly slow startup. These are all signs your once-proud PC might be on its last legs. But before you toss it and shell out for a shiny new machine, consider this: repair versus replace.
The answer like that perfect meme, depends. Here’s a breakdown of the factors to consider when deciding on your PC’s fate:
The Age Game: Generally, younger PCs are better repair candidates. For machines under 3 years old, a simple fix like a RAM upgrade or a new hard drive can breathe new life into them. However, for PCs pushing a decade, repairs might become a money pit, constantly playing catch-up with declining performance.
The Dollar Dilemma: Repair costs vary wildly depending on the problem. A quick software fix might be a steal, while a motherboard replacement could cost more than a budget-friendly new PC. Get a diagnosis from a trusted repair shop (or watch some DIY repair tutorials online) to estimate the repair cost.
The Performance Puzzle: Is your slow PC a constant source of frustration? Upgrading key components like RAM or the SSD or HDD or the graphics card can offer a significant performance boost. However, if your needs have drastically changed (think: casual browsing vs. high-end video editing), a new, used or refurbished PC with more powerful hardware might be a wiser investment.
The Eco-Ethical Edge: Don’t underestimate the environmental impact. Repairing your PC extends its lifespan, keeping e-waste out of landfills. If you do choose to replace, consider recycling your old PC or selling it for parts.
The Data Divide: Moving data to a new PC can be a hassle, especially with large files or complex setups. If you’re comfortable transferring data yourself or willing to pay for professional help, this might not be a major concern.
The DIY Dilemma: If you’re tech-savvy and comfortable tinkering, some repairs might be DIY projects. However, for complex issues, a professional’s touch can save you time, frustration, and potentially even further damage.
Ultimately, the decision hinges on your budget, your PC’s age and repairability, and your specific needs. By carefully considering these factors, you can choose the most cost-effective and environmentally responsible path, whether it’s a repair that keeps your old friend chugging along or a fresh start with a brand new PC.
Is it Safe to Take Your Computer to a Repair Shop? A Trustworthy Tech Tune-Up or Privacy Peril?
 The dreaded computer gremlin strikes. Your once-loyal machine sputters, groans, or refuses to budge altogether. Panic sets in, but a beacon of hope appears: the computer repair shop. Yet, a nagging doubt lingers – is it safe to entrust your precious device, brimming with personal information, to a stranger?
The dreaded computer gremlin strikes. Your once-loyal machine sputters, groans, or refuses to budge altogether. Panic sets in, but a beacon of hope appears: the computer repair shop. Yet, a nagging doubt lingers – is it safe to entrust your precious device, brimming with personal information, to a stranger?
The answer, like most things in tech, is nuanced. Repair shops can be lifesavers, but navigating them requires caution. Here’s a breakdown of the risks and how to mitigate them:
The Data Domino Effect: Your computer harbors your documents, photos, and maybe even financial records. Unethical technicians could exploit this access.
Safeguard Strategy: Back up your data religiously. Cloud storage or external hard drives are your friends. If critical information remains, consider removing it before the shop visit (consult a professional for secure deletion methods if needed).
The Parts Prank: Replacing faulty components is a common repair, but some shops might install used or lower-quality parts, inflating your bill or compromising performance.
Transparency is Key: Ask about parts beforehand. Request genuine parts from reputable brands and get a written quote specifying what’s being replaced.
The Phantom Fix: Beware of shops that diagnose unnecessary repairs or inflate problems.
Knowledge is Power: Research common issues for your computer model. Be clear and concise when describing the problem. Don’t be afraid to get a second opinion if the diagnosis sounds fishy.
Finding the Trustworthy Techie: Not all repair shops are created equal.
Reputation Matters: Research online reviews and ask friends for recommendations. Look for shops with certifications from major tech brands.
Ask Questions: Don’t be shy! Inquire about their repair process, data security practices, and warranty policies. A shop comfortable answering your questions is likely a good sign.
By following these steps, you can transform your computer repair shop visit from a gamble into a strategic move. With a little preparation and the right shop, your computer will be back in fighting form, minus the security scare.
For more information call our computer repair shop in louisville, KY at (502)963-3981
The Perfect Storm: Why Crippling Cyberattacks are on the Rise
 Crippling cyberattacks, particularly ransomware assaults, are plaguing businesses and government agencies across industries. From private healthcare providers to critical infrastructure like pipelines, no entity seems immune. This alarming trend isn’t a random surge; it’s a confluence of factors creating a perfect storm for cybercriminals.
Crippling cyberattacks, particularly ransomware assaults, are plaguing businesses and government agencies across industries. From private healthcare providers to critical infrastructure like pipelines, no entity seems immune. This alarming trend isn’t a random surge; it’s a confluence of factors creating a perfect storm for cybercriminals.
1. The Exponential Growth of Valuable Data: Businesses and governments hold a treasure trove of sensitive data – financial records, patient information, intellectual property – and this data is a goldmine for attackers. Ransomware encrypts this data, rendering it inaccessible until a ransom is paid. The more valuable the data, the higher the ransom demanded, leading to crippling financial losses for victims.
2. The Evolving Threat Landscape: Cybercriminals are constantly innovating. Gone are the days of basic phishing emails. Today’s attacks are sophisticated, exploiting vulnerabilities in complex IT systems and leveraging social engineering tactics to bypass even the most well-trained employees.
3. The Remote Work Revolution: The shift to remote work during the pandemic created a larger attack surface for businesses. Employees accessing corporate networks from unsecured home environments introduces new vulnerabilities. Additionally, the increased reliance on cloud-based tools expands the potential entry points for attackers.
4. The Rise of Ransomware-as-a-Service (RaaS): Cybercrime has become an industry, with RaaS platforms offering easy-to-use ransomware tools to anyone with an internet connection. This democratizes cyberattacks, making them accessible to a wider range of criminals, not just highly skilled hackers.
5. The Allure of Easy Money and Low Risk: The success rates for cyberattacks, particularly ransomware, are concerningly high. The potential for significant financial gain, coupled with the relatively low risk of getting caught due to the global and anonymous nature of the internet, makes cybercrime a tempting proposition for malicious actors.
6. The Vulnerability of Outdated Infrastructure: Many businesses and government agencies struggle to keep pace with the ever-evolving cyber threat landscape. They rely on outdated IT systems with known vulnerabilities, making them easy targets for attackers.
7. The Lack of Cybersecurity Awareness: Human error remains a significant factor in cyberattacks. Phishing emails and social engineering tactics continue to be effective because employees may not be adequately trained on cybersecurity best practices.
8. The Digital Divide in Leadership: In an increasingly digital world, a leadership gap exists where those in power may not fully grasp the intricacies of cybersecurity threats. This lack of understanding can hinder proactive measures and make it difficult to allocate appropriate resources to address cyber vulnerabilities.
What Can Be Done?
There’s no silver bullet, but a multi-pronged approach is crucial. Businesses and government agencies need to invest in robust cybersecurity infrastructure, prioritize employee training, and implement strong data backup and recovery plans. Additionally, international cooperation to track down cybercriminals and disrupt their operations is essential.
Bridging the Digital Divide: Encouraging a more digitally literate leadership class is crucial. This can be achieved through targeted training programs, fostering a culture of innovation within government, and potentially even considering age limitations for certain positions.
By acknowledging the reasons behind the rise of cyberattacks, businesses and government agencies can take proactive steps to defend themselves and mitigate the potential for crippling disruptions. The future of cyberspace may be uncertain, but vigilance, a commitment to robust cybersecurity, and a digitally informed leadership are the best weapons we have in this ongoing battle.
Windows Through Time: A Journey Across the Panes of Microsoft’s Evolution
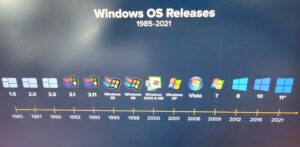 One of my interview questions is always: “name all the Windows operating systems since XP.” And overall, I’m a fan of Microsoft and Bill Gates and the late Paul Allen. In the vast landscape of digital innovation, Microsoft Windows stands as a towering giant, shaping the way we have interacted with computers since Gates purchased 86-DOS for $50,000. From humble beginnings to a ubiquitous presence in homes and offices worldwide, the history of MS Windows is a fascinating tale of technological advancement and digital design.
One of my interview questions is always: “name all the Windows operating systems since XP.” And overall, I’m a fan of Microsoft and Bill Gates and the late Paul Allen. In the vast landscape of digital innovation, Microsoft Windows stands as a towering giant, shaping the way we have interacted with computers since Gates purchased 86-DOS for $50,000. From humble beginnings to a ubiquitous presence in homes and offices worldwide, the history of MS Windows is a fascinating tale of technological advancement and digital design.
Genesis of Windows:
The Windows saga technically began in 1981 with 86-DOS and then went into widespread adoption in 1985 with the advent of Windows 1.0, a graphical extension for MS-DOS. Though not an instant hit, it laid the groundwork for a revolutionary approach to computing. The introduction of a graphical user interface (GUI) marked a departure from the command-line interfaces of the past, making computing more accessible to a broader audience.
Windows 95: The Game-Changer:
Windows 95, often hailed as a milestone in Microsoft’s journey, hit the shelves in, unsurprisingly, 1995. This release introduced the iconic Start menu, taskbar, and a simplified user interface, making it a user-friendly environment for millions. The graphical overhaul set a new standard for personal computing, and the CD-ROM distribution brought it to the masses.
The Millennium Misstep:
Windows ME (Millennium Edition) followed in 2000, attempting to bridge the gap between the 9x series and the NT-based systems. However, plagued by stability issues, it failed to capture the success of its predecessors. Despite its shortcomings, Windows ME laid the groundwork for future innovations in multimedia and system restoration features.
XP: The Long-Lasting Legacy:
Windows XP, released in 2001, became a symbol of stability and user-friendliness. Its longevity was unprecedented, with support lasting until 2014. XP not only refined the Windows experience but also introduced features like System Restore and a fresh visual style. Its enduring popularity makes it one of the most beloved Windows versions.
Vista and 7: Peaks and Valleys:
Windows Vista, launched in 2007, faced criticism for its performance issues and hardware demands. However, it laid the foundation for Windows 7, released in 2009, which redeemed Microsoft’s reputation. Windows 7 refined the Vista experience, offering improved performance, a streamlined taskbar, and enhanced security features.
Windows 8: A Touch of Controversy:
Windows 8, released in 2012, aimed to bridge the gap between traditional PCs and touchscreen devices. Its radical departure from the familiar Start menu stirred controversy, but it marked a significant step toward a unified experience across various device types. The subsequent Windows 8.1 addressed user concerns, bringing back the Start button.
Windows 10: A Unified Ecosystem:
Launched in 2015, Windows 10 emerged as a synthesis of the best elements from previous versions. It introduced a seamless ecosystem, with a universal app platform and a return to the familiar Start menu. Windows 10 also embraced a continuous update model, ensuring users had access to the latest features and security enhancements.
The Future of Windows:
As technology continues to evolve, Microsoft remains committed to the Windows platform. With innovations like Windows 11 and beyond, the focus is on enhancing user experiences, optimizing performance, and adapting to the changing landscape of computing.
Conclusion:
The history of MS Windows is a captivating narrative of innovation, adaptation, and user-centric design. From the early days of Windows 1.0 to the latest iterations, Microsoft’s flagship operating system has played a pivotal role in shaping the digital era. As we peer into the future, the Windows story is far from over, promising continued evolution and groundbreaking developments.
Navigating Legal Responsibilities: A Guide for Computer Repair Businesses
 In the rapidly evolving landscape of technology, computer repair businesses play a crucial role in ensuring the smooth functioning of devices and safeguarding valuable data. Louisville Laywer John Olash says: “While the focus is often on technical expertise, it’s equally important for computer repair shops to navigate the intricate web of legal responsibilities.” This guide aims to shed light on the key legal obligations and responsibilities that computer repair businesses should be aware of to operate ethically and within the bounds of the law.
In the rapidly evolving landscape of technology, computer repair businesses play a crucial role in ensuring the smooth functioning of devices and safeguarding valuable data. Louisville Laywer John Olash says: “While the focus is often on technical expertise, it’s equally important for computer repair shops to navigate the intricate web of legal responsibilities.” This guide aims to shed light on the key legal obligations and responsibilities that computer repair businesses should be aware of to operate ethically and within the bounds of the law.
1. Data Protection Laws
Overview:
Data protection is a paramount concern in the digital age. Repair shops often handle sensitive customer data, making it imperative to comply with data protection laws. Familiarize yourself with local and national regulations, such as the General Data Protection Regulation (GDPR) or the Health Insurance Portability and Accountability Act (HIPAA), depending on your jurisdiction and the nature of the data you handle.
Practical Tips:
Obtain explicit consent from customers before accessing or storing any personal or sensitive information.
Implement robust data security measures to prevent unauthorized access or data breaches.
Regularly update privacy policies to reflect any changes in data handling practices.
2. Customer Privacy
Overview:
Respecting customer privacy is not just good business practice; it’s a legal requirement. Repair technicians must strike a balance between providing effective services and preserving the confidentiality of customer information.
Practical Tips:
Louisville attorney John Byrnes says “Clearly communicate your privacy policy to customers and ensure they understand how their data will be handled.
And restrict access to customer information only to authorized personnel.”
Train staff on the importance of customer confidentiality and data protection.
3. Consumer Rights
Overview:
Understanding and respecting consumer rights is essential for building trust and avoiding legal complications. Consumers have rights regarding the quality of service, timely repairs, and transparent pricing.
Practical Tips:
Provide clear and detailed estimates before commencing repairs, including potential additional costs.
Clearly outline warranty terms and conditions to manage customer expectations.
Respond promptly to customer inquiries and complaints, addressing any concerns with transparency.
4. Documenting Repairs and Transactions
Overview:
Maintaining accurate records of repairs and transactions not only ensures transparency but also serves as a legal safeguard in case of disputes.
Practical Tips:
Develop a standardized system for documenting repairs, including the issues identified, services provided, and any replaced components.
Issue detailed invoices that include a breakdown of charges, ensuring clarity for both parties.
Retain records for a legally required period, as per local regulations.
Conclusion
In the world of computer repair, technical proficiency must go hand-in-hand with legal compliance. By proactively addressing data protection, customer privacy, consumer rights, and documentation practices, computer repair businesses can build a solid foundation for ethical operations. Staying informed about the legal landscape and regularly updating policies will not only protect the business but also foster trust with customers. As technology continues to advance, navigating legal responsibilities will remain a cornerstone of successful computer repair businesses.
Demystifying Tech Jaron: A Glossary of Common Computer Terms
 Technology has become an integral part of our daily lives, but its complex vocabulary can sometimes be overwhelming and confusing. We often encounter unfamiliar terms and acronyms that leave us scratching our heads. To help demystify the jargon, here’s a glossary of common computer terms that everyone should know.
Technology has become an integral part of our daily lives, but its complex vocabulary can sometimes be overwhelming and confusing. We often encounter unfamiliar terms and acronyms that leave us scratching our heads. To help demystify the jargon, here’s a glossary of common computer terms that everyone should know.
1. Operating System (OS): Software that manages computer hardware and software resources and provides common services for computer programs. Examples include Windows, macOS, and Linux.
2. Browser: A software application used to access and view websites on the internet. Popular browsers include Google Chrome, Mozilla Firefox, and Apple Safari.
3. Firewall: A network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. It acts as a barrier between a trusted internal network and an untrusted external network, such as the internet.
4. Cloud Computing: The delivery of computing services—including servers, storage, databases, networking, software, and analytics—over the internet (“the cloud”) to offer faster, more flexible, and scalable resources.
5. Cookies: Small pieces of data sent from a website and stored on a user’s computer by the user’s web browser while the user is browsing. Cookies are used to remember state information or to record the user’s browsing activity.
6. Virus: A type of malicious software program that, when executed, replicates by modifying other computer programs and inserting its own code. Viruses can cause harm to a computer system, such as corrupting data or stealing personal information.
7. Router: A networking device that forwards data packets between computer networks. Routers perform the traffic directing functions on the internet by sending data to its intended destination based on the IP address and other routing information.
8. RAM (Random Access Memory): A form of computer memory that can be read and changed in any order, typically used to store data temporarily while a computer is running. In simple terms, RAM is what allows a computer to multitask and run programs efficiently.
9. URL (Uniform Resource Locator): The address used to access resources on the internet, such as a website or a file. A URL indicates the protocol used to access the resource, the location of the server, and the specific file or resource being accessed.
10. Encryption: The process of converting information into a code to prevent unauthorized access. Encryption protects sensitive data by rendering it unreadable to anyone without the necessary decryption key.
11. Bluetooth: A wireless technology standard for exchanging data over short distances from fixed and mobile devices, creating personal area networks (PANs). It is commonly used for connecting devices such as smartphones, headphones, and speakers.
12. Cache: A hardware or software component that stores data so that future requests for that data can be served faster. Caching can significantly improve the performance and responsiveness of a system.
13. Ethernet: A system for connecting a number of computer systems to form a local area network (LAN), with protocols to control the passing of information and to avoid simultaneous transmission by two or more systems.
14. HTML (Hypertext Markup Language): The standard markup language for documents designed to be displayed in a web browser. It can be assisted by technologies such as Cascading Style Sheets (CSS) and scripting languages such as JavaScript.
15. VPN (Virtual Private Network): A secure and private connection that enables users to send and receive data across shared or public networks as if their computing devices were directly connected to a private network. VPNs are commonly used to protect online privacy and secure internet connections, especially when using public Wi-Fi networks.
Understanding these common computer terms can empower individuals to navigate and comprehend the world of technology more confidently. As technology continues to evolve, having a foundational understanding of these terms will help bridge the gap between the tech-savvy and those less familiar with the fast-paced and ever-changing landscape of digital innovation.
When Buying A New PC Do Not Focus On Intel i3, i5, or i7 Designation
 When it comes to choosing a new computer or laptop, the processor is often one of the most important factors to consider. Intel’s processors, particularly the i3, i5, and i7 series, are some of the most popular and widely used in the industry. However, many people overlook the significance of the numbers that come after these designations, which actually represent the generation of the processor. Focusing on the generation of the processor is crucial for several reasons.
When it comes to choosing a new computer or laptop, the processor is often one of the most important factors to consider. Intel’s processors, particularly the i3, i5, and i7 series, are some of the most popular and widely used in the industry. However, many people overlook the significance of the numbers that come after these designations, which actually represent the generation of the processor. Focusing on the generation of the processor is crucial for several reasons.
First and foremost, the generation of the processor tells you the age. I’ve noticed recently especially on Amazon people are trying to pass off computers as new that are acutally “renewed” or used or have NOS (new old stock) parts in them. Hey, there is nothing wrong with a 8th Gen i7, or 9th Gen, it’s just important to know that it is not the same as a 12th gen. If you’re buying it on Amazon or Ebay and it’s a 8th gen something is up.
In addition, the generation of the processor can also affect its compatibility with other hardware and software. Newer generations of processors often come with updated architectures and instruction sets, which can lead to better compatibility with the latest hardware components and software applications. This is particularly important for tasks such as gaming, video editing, and 3D rendering, where compatibility and performance capabilities are critical.
Furthermore, focusing on the generation of the processor is essential for future-proofing your investment. By choosing a newer generation processor, you can ensure that your computer or laptop will remain relevant and capable for a longer period of time. This is particularly important for those who rely on their devices for demanding tasks or for professional use, as the performance gap between newer and older generation processors continues to widen over time.
It’s also worth noting that newer generations of processors often come with enhanced security features, which can be crucial for protecting sensitive data and maintaining the integrity of your system. As cyber threats continue to evolve and become more sophisticated, having a processor with the latest security capabilities is essential for safeguarding your digital assets and privacy.
In conclusion, the numbers that come after Intel’s i3, i5, and i7 designations represent the generation of the processor, and focusing on these numbers is crucial for ensuring optimal performance, compatibility, and future-proofing. Whether you are in the market for a new computer or looking to upgrade your existing one, considering the generation of the processor is an important factor in making an informed and effective decision. By staying informed about the latest advancements in processor technology, you can ensure that you are getting the best possible performance and features from your device.
If you need help buying a new PC in Louisville Kentucky or surrounding areas feel free to give me a call at (502)963-3981


