It seems that nearly everyone has had the misfortune of dealing with a computer virus by now. If your computer has ever been infected with a computer virus, you know firsthand just how inconvenient and potentially damaging it can be. And then there is the expense of having to have and pay for professional virus removal. There are thousands of computer viruses floating around the Internet with cyber-criminals developing more every day. Fortunately, there are many things you can do to protect yourself. As with many other aspects of life, having the proper habits in place is the best way to ensure success.
Avoid these five mistakes and you’ll be on the right track:
1. Failing to install and use an up-to-date anti-virus program.
It’s true that these programs consume a considerable amount of system resources. However, the consequences of a computer virus are well worth the slight hassle of losing a few CPU cycles. Being ‘smart’ isn’t an acceptable substitute for having a high quality anti-virus program in place. Not for most people at least.
• Ensure that any anti-virus program you’re using is updated on a regular basis. Ensure that it has “real time” protection. Malware and Viruses are constantly being developed and updated. It’s important that your defense is constantly being improved and updated, too.
2. Assuming that an anti-virus program is foolproof.
Most computer users simply have too much faith in the programs that provide protection from malware. Consider the fact that in many cases, computers have to been infected with new viruses before anti-virus program manufacturers can develop solutions to prevent them. Therefore, you might not have the protection you “think” you do. A high quality anti-virus program isn’t an acceptable substitute for researching ways to avoid viruses and constantly developing new web browsing skills and habits.
3. Downloading free software, movies, music, etc.
There are financial advantages to obtaining software, movies, music and games for free, but there are also significant risks. Those that are interested in spreading a computer virus use pirated software as a tool to deliver these malicious programs. You’re not just getting a free movie; you’re also providing the perfect opportunity for a virus to infect your computer. Proceed with caution when anything is free on the internet.
4. Blindly opening email attachments. While most email programs effectively screen email attachments for viruses, it’s generally a good idea to ignore email attachments from unknown senders. This is especially true when dealing with executable files. Consider the source and control your curiosity.
5.Clicking on any popup that states your computer has a virus.
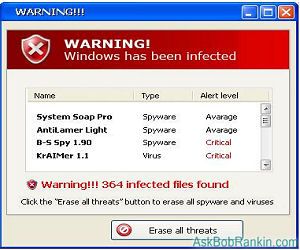
Those annoying popups are a common source of computer viruses. The best solution is to close your browser without clicking on that pesky popup. You can press ALT F4 to close a window without clicking on a pop-up. This common type of infection claims to be the solution to the very problem it’s creating. In most cases, the offered solution will cost you a considerable amount of your hard-earned money.
Few things can disrupt your peace of mind as effectively, or as quickly, as having to stop your busy schedule and call a computer repair professional and schedule a virus removal. Staying safe online requires more than the use of an anti-virus program. The user is always the one variable that can never be completely secured. It’s difficult to protect you from yourself. Diligence and research are important. Spend some time noodling around on the internet for articles on how improve your web browsing skills and habits and reading about how to avoid computer viruses. And, I hope avoiding the five habits above is an good start.
Author Archives: Chris Calkins
XP Support Ends on April 8th, 2014 – What this means for XP Users….
Windows XP is the second most successful operating system produced by Microsoft thus far (only Windows 7 has been better received). First released on October 24th, 2001, Window XP has approximately 500 million users globally who still use this operating system. For over a decade now, the XP support provided by Windows has been a major reason for its success and user satisfaction. Three service packs were released by Microsoft for XP. Nevertheless, all good things much come to an end. And Microsoft will be ending support effective from April 8th, 2014. What does this mean for those millions of users who are still using XP on their computers?
No more XP Patches
With XP support gone no more patches for XP will be released. Patches are normally designed to fix problems or update software related to the operating system. They also provide security updates and improve OS performance. Without these patches an outdated OS is more vulnerable to malware and other virus infections. No security fixes means anyone running XP stands a greater chance of being becoming infected and also having data stolen.
No more Driver Updates
Drivers are pieces of software that run various parts of your computer such as your keyboard, monitor and USB Ports, for example. Manufacturers of machine components create software to run the components, then release these software and updates to the computer manufacture to put on their website. When an OS stops support and updates the component manufactures also stop releasing driver updates. Therefore, in time XP users may start finding it difficult to use a XP computers at all as the individual components on the machine may start to become “glitchy” (start to malfunction).
What are the options?
If you are an individual who uses XP on your home computer for basic use, you may try and move to Windows Vista or Windows 7. It might also be time to consider replacing your computer. In general, the decision to withdraw XP support is beening looked upon by some users as Window’s last effort to force users and enterprises to move from XP to Windows 7 or 8. Whatever the reason, if you’re a “tried-and-true” Windows XP fan and hold-out — you should accept the inevitable — your time with XP is limited….
Top Reasons Motherboards Fail
 The motherboard is the heart of a computer. As long as your computer’s motherboard is intact – when things go wrong – your computer is often repairable at a reasonable cost. Motherboard repair or replacement, on the other hand, is usually very expensive. That said, there are several things to think about regarding prolonging the life of your motherboard. Here is a list of different reasons your computer’s motherboard might fail — along with suggestions on failure prevention.
The motherboard is the heart of a computer. As long as your computer’s motherboard is intact – when things go wrong – your computer is often repairable at a reasonable cost. Motherboard repair or replacement, on the other hand, is usually very expensive. That said, there are several things to think about regarding prolonging the life of your motherboard. Here is a list of different reasons your computer’s motherboard might fail — along with suggestions on failure prevention.
PC Builder Damage
At least once a month I get a call from a PC Builder saying he or she just build a computer and it won’t come on. A nontrivial amount of the time the motherboard or CPU has bent pins or other damage such as: scratching or cracking the PCB, bent PCIe lanes, bent over capacitors etc. This could often be mitigated by the building watching Youtube videos about the build rather than forcing it.
Electrical Spikes and Surges
An electrical spike or surge is a short-lived burst of energy in an electric circuit. This can be the result of power hungry appliances, problems with wiring, problems with the power service outside the house, or the result of a lightning strike. Lightning is the #1 culprit of spike/surge motherboard failure I see — and it will often go in through the Ethernet port and bypass a surge protector! This sudden change of voltage can cause damage to the delicate circuits in a motherboard. Connecting your computer to a power outlet that has frequent fluctuations in electrical output may also cause damage to your motherboard. Though at times immediate damage may not be visible, it may harm the motherboard over time. To protect your motherboard from electrical spikes, use a high quality surge protector that can neutralize the effects. Unfortunately, it’s difficult to protect from lightning strikes.
Dust, Pet Hair and Debris
Dust pet hair and debris can be a sure motherboard killer. At my shop in Louisville, KY I can’t tell you how many times I see fans and fan basins clogged with dirt, dust, and debris. When these things collect in your machine, they start blocking the air circulation that keeps the machine cool. It is like harmful fat that blocks your arteries that cause a heart attack. A computer intake pulls all these things in when the fans rotate. This leads to blocking the airflow, which causes overheating.
Cigarette smoke
Tar from cigarette smoke (it’s not the nicotine, by the way) is not good for your health and also for the health of your computer. Cigarette smoke, when combined with dust produces a sticky gooey substance inside a computer. It smells bad and is also very difficult to remove. This tar can cause overheating — which may damage the motherboard. It is recommended that you have a periodic schedule of cleaning the interior of your computer (at a qualified shop) and try and keep it away from cigarette smoke.
Heating Issues
Overheating of the motherboard can occur if multiple operations are performed simultaneously and power supply is continuous (give your computer a periodic rest if gaming, watching videos, etc). Also, clogging of fans can cause a motherboard to overheat. In some cases, overheating may also occur due to fluctuations in power supply or in one of the parts of the motherboard circuit. Finally, using a laptop in your lap or on another soft surface can cover up intakes and exhaust fans causing your machine to heat up. Overheating can be prevented by keeping the fan basins clear, giving your computer a rest after heavy use, using your laptop in the cooler rooms in the house, and using it on a cold hard surface. Temperature monitoring software can be installed to monitor the temperature of your computer internally (Core Temp, Real Temp, SpeedFan).
Impact or Spill
An accidental impact to your motherboard can cause severe damage to the circuits which may cause motherboard failure. I have seen motherboards fail immediately due to impact from drops. Spill damage is also quite common. I have seen every type of liquid kill a motherboard instantly but thicker liquids (e.g., milk) seems to be the worst. Spills can cause your motherboard to short out instantly. Water can also cause damage to the different chips on your motherboard causing your motherboard to fail. If you do spill something into your laptop do NOT turn it on again and take it to a qualified computer repair shop, immediately.
Manufacturer Design Defects
Motherboards are mass produced and there are chances that manufacturing defects occur. Cheap motherboards also tend to fail more quickly. The capacitors installed may be faulty and may cause problems. The bus architecture of the board may have been engineered incorrectly and there might be cooling issues. Most motherboards come with a warranty so it should take care of expenses if problems arise during the warranty period, but that is often only a year and doesn’t cover user generated problems, of course. Sometimes the manufacturers admit to the faulty designs but usually not. Usually computer repair shops can tell if there is a “known issue” because we see the same problems occurring over and over with the same make and model of computer. I can see some trends related to certain generations of computers and it’s not with only one manufacturer. Sometimes these manufacturer defeats aren’t “known” for years (after enough of a make and model show up at the shops and enough complaints are filed that it becomes obvious there is a known issue with a particular make and model) and then it becomes more obvious based on discussions on the internet.
Normal Aging and Wear
Your motherboard will eventually fail (if something else doesn’t fail first.) This is a fact. It is an electric circuit board and has a finite life span. Some good motherboards will give you around fifty thousand hours of work time or even more if taken care of properly. Once they have reached their useful life span, they do fail and you may have to replace it or replace your computer. The good news is when you are aware of the reasons motherboards fail preventative and preparatory actions (see my article on backing up important files) can be taken to minimize the negative impact.
Please visit our website for more useful computer repair and topics.
What’s the Best Backup? – Cloud vs. External
Data backup is one of the most important processes for any individual, enterprise, government organization or non-profit. Data is critical. Data is not your programs or apps. You can reinstall those with discs and reenter your license number for it. What matters are the files you created with that software. For most people this means your photos, documents and spreadsheets, and music. And if you’re a business your accounting file. Of course these need to be protected against loss loss or damage. So how do you do that exactly? It is called “redundancy.” You need to have those file in at least two places. They are already on your computer and you should have them on another device in case of a catastrophic event with your computer or facility.
And, please allow me to demystify something about the cloud. It’s just another device. It’s another device at someone else’s location. Nothing more and nothing less. Your data is not floating around in the sky. So, you only have to decide if you want to send your data elsewhere for backup or if you’re capable of doing your own backup on site. I do my own back-up and it is very, very easy but below I’ll lay out the advantages and disadvantages of both types so you can make in informed decision.
Cloud Backup
Advantages
Ease of access – Armed with just a login id and password you can access all your files anytime, anywhere with ease. Although I’m not sure why you would want to do this. It’s a back-up right?
Security – No worries of your data being stolen or lost in a fire. Your files are securely encrypted and made available only to those who you permit to access.
Disadvantages
Speed – Data transfer depends on the speed of your internet connection. If there are big files to be transferred and a slow internet connection you may have to cultivate patience.
Cost – You need to pay on a monthly or a yearly basis, though the charges may be low it needs to be considered based on your usage.
Control – You do not have full control over your data. If your service provider decides to run maintenance on the storage, you can hardly do anything but wait for the system to start again.
External Hard Drive or Flash Drive Back-Up
Advantages
Cost Effective & Simple – The prices for storage is fast decreasing. A 2 TB (which is an absurd amount of storage) external hard drive will cost you around $120 USD at Amazon.com or Ebay and if you ever need to increase your storage all you need to do is replace the existing one with a higher storage capacity.
Speed – A transfer speed of USB 3.0 means huge amount of data can be transferred in just a matter of minutes or hours.
Security – With an external hard drive you are in total control of your data. You can protect it with a password which means you are the only one who can access it.
Simplicity – You don’t’ need to use the automatic backup feature of your external hard drive or flash drive. I prefer to simply drag and drop my data. Then 30 days later, I delete the information on the external device and drag and drop the updated folders again. Very smart and simple
Disadvantages
Security – Though your data can be securely encrypted, you always run the risk of losing your hard drive or someone else stealing it. But I think this is not likely.
Technical Problem – With the external hard drive you always run the possibility of the drive failing or crashing. But if you have redundancy in data (remember this from earlier) you have one copy at all times.
Onsite – If you have a fire it is possible that both of your devices will be destroyed. All you have to do to prevent his is put a third copy on a flash drive in your bank box.
What is the best then? Both of these methods have their own benefits and drawbacks. It comes down to what you prefer. For most circumstances it is not necessary to do a cloud backup, in my opinion. But the pros and cons are above so now you can make an informed decision.
For more information on data backup or data recovery in Louisville, KY click on these links.
Computer Services
Computer Service and Customer Service is what we are about.
Whatever you can imagine going wrong with your technology, we’re here to fix it. From printer problems and software issues to power supply trouble and router swaps, we’ve got you covered. Our professional techs have performed hundreds of break/fix server repairs and a myriad of various other business service calls. We have the experience and expertise to solve any computer technology problem you may have.
Once your hardware or software is repaired we can even reconfigure your entire IT system with new free software and put all your company data back in place. Whether you need a router or a virus removal, no problem you may have with your business technology is too big or too small for us. On-Site Louisville Computer Repair Co. can be your one stop shop for on-site business computer service in Louisville, KY and surrounding areas.
Some business computer services we provide:
Network setup and management
Hardware procurement and installation
Software installation and configuration
IT helpdesk and technical support
Data backup and recovery
Cloud computing services
Virtualization solutions
Cybersecurity services and solutions
Firewall setup and management
Network monitoring and maintenance
Server administration and maintenance
Email hosting and management
VoIP (Voice over Internet Protocol) services
Website development and hosting
Domain name registration and management
Database design and management
Remote desktop services
IT consulting and technology planning
IT project management
Mobile device management (MDM)
Internet connectivity and WAN optimization
Network infrastructure design and implementation
VPN (Virtual Private Network) setup and management
Software licensing and compliance management
Software updates and patch management
Disaster recovery planning and testing
Network security audits
Malware and virus protection
Intrusion detection and prevention
Data encryption services
IT asset management
Printer and peripheral device support
Unified communications solutions
Video conferencing services
Business process automation
Data analytics and business intelligence
IT training and user education
Social media management tools and services
Customer relationship management (CRM) software
Enterprise resource planning (ERP) systems
Point of sale (POS) systems
Inventory management software
Supply chain management software
Human resources management software
Accounting and financial management software
Time tracking and project management tools
Document management and collaboration tools
Virtual private server (VPS) hosting
Dedicated server hosting
Content delivery network (CDN) services
Virus Removal 101 –Keeping Your Computer Free of Infections
Virus removal can be a difficult task even for the tech-experts and some viruses can resist removal. If your computer is playing sounds, moving extremely slow or taking you to wrong websites I recommend you seek a qualified computer repair shop for removal. If on the other hand your computer is running well and you want to do a routine virus scan here are some tips to keep your computer free of infections. You should do a weekly virus scan with a powerful malware removal tool (not your antivirus software suite) such as Malwarebytes free edition which I will explain in detail below.
Start in Safe Mode
Safe mode is used for troubleshooting issues and runs only the minimum software and drivers necessary to start your computer. To start in safe mode you should remove all the CDs, floppies, or USB storage from your computer and restart. Press and hold the F8 key while the computer is restarting. You need to press F8 before the Windows logo is shown. If it appears before you press F8, then you need to go through the entire restart cycle again. You will be shown a black screen with white lettering and an advanced boot option menu. Use the down arrow to select “safe mode with networking” and hit enter.
Remove Any Suspicious Programs from Control Panel
You should manually remove any suspicious programs from your computer using the control panel. The file path in Windows 7 is: Start > Control Panel > Add/Remove Programs. Make sure you know what you are removing and take precautions not to remove any of your system software that is critical for your machine to run correctly or application software that you use which is “non-problematic.” I especially target games, toolbars and media players for removal. If you have a question about what an application does “Google It.”
Remove Aftermarket Browsers and Reset IE
I recommend removing aftermarket browsers such as Chrome and Firefox and resetting Internet Explorer by following the below steps. To remove Chrome and Firefox go back to Start > Control Panel > Add/Remove Programs. Internet Explorer can be reset in control panel too. The file path in Windows 7 for resetting IE is Start > Control Panel > Networking and Sharing >Internet Options > Advanced Tab.
Run Malwarebytes Free Edition and Restart
The Malwarebytes is a free Anti-Malware program, which features high speed scanning and removal of the suspicious Malware on your computer. If not installed, you can download it free from the internet at http://www.malwarebytes.org. Be sure to stick with the free version and do not enable the Pro Version (uncheck checkbox for pro). Once installed, select full scan. After the scan if finished check the box by the infections and click remove. Restart your computer.
Three Common Laptop Repairs and How to Avoid Them
At my computer repair shop in Louisville I see these three problems over and over. Sometimes it is the result of normal wear-n-tear. Parts wear out, right? And there are plenty of lemon parts with computers. I’ve seen a new hard drive fail in the first thirty days of use, for example. But sometimes accidents happen. And, often mistakes are made due to the fact that people don’t know how to properly maintain and handle their computer equipment. This article will make you aware of lurking dangers so you can avoid accidents and maintain your equipment properly, and avoid these costly and preventable laptop repairs completely.
DC Jack Repair
DC Jacks or charging ports take a lot of abuse. I know I’ve had several ignitions in my car replaced over the years. When I was a starving college student I remember one winter I would spray deicer in the ignition so my key would work. It got me through the winter, but finally I had to replace the ignition. The DC Jack on a laptop is the hole where the power adaptor or “charger” plugs into the computer. In most laptop units, the DC jack is directly soldered onto the motherboard — which not only makes it delicate but also expensive to repair. Often the entire laptop has to come apart to do the repair as there is no access anywhere around the jack. The three most common reasons the jack breaks is: 1.A child or animal trips on the cord. 2. People jerk the cord out hard and at an angle and do not realize it is not that difficult to break a solder joint and 3. People travel — either across the room or across the city — with the charger still connected to the laptop. Don’t do it!
Screen Repair
Perhaps even more common is laptop screen repair and replacement. I have seen laptop screens break when someone picked up a laptop by the corner of the screen to move it off of the floor up onto a table. Their thumb went right through the screen. I almost did it once myself. It is a very delicate screen. It does not have to be a dropped or take a hard impact to cause a cracked laptop screen. Another common scenario is closing something in the laptop. A mouse, a letter opener, even a flash drive left on the keyboard when the laptop is closed can cause a screen to break or fail. It is an expensive repair depending on the laptop screen and computer make and model. So, be aware of this “soft spot” on your laptop and be extremely gentle with it.
Motherboard Failure
Perhaps the most expensive and devastating, but rather common laptop repair is motherboard repair. This is what I consider a “catastrophic event” in the computer repair business. The entire machine has to come apart, the board taken out, and repaired at the microscopic level with expensive equipment. Sometimes this part simply fails, but often it is the result of what’s known in the industry as a “thermal event.” That is a heat related issue. To prevent this from happening, keep your laptop computer as cool as possible. Despite the name, a laptop should NOT be anyone’s lap. While the exhaust fan for the CPU is often located on the side of a laptop, the air intake is often located on the bottom. If your laptop is on your lap you are probably covering up the air intake for your exhaust fan which is extremely dangerous. You want to keep your laptop on a flat, cold, hard surface at all times! You can install free software such as the core temp monitor (be careful not to get a virus infection when you’re downloading free utilities) to monitor the actual temperature of your laptop from the inside. Also you can leave the battery out. I’ve never even had a battery in my laptop it’s still in plastic. It is not necessary to power a laptop that is plugged in to a wall outlet and only generates more heat. Keep the fan basins blown out with compressed air – especially if your home is dusty or you have dogs or cats. And as the computer starts to age if the heat monitor utility shows your laptop heat is on the rise, you can even go to the power options and turn your processor down a bit. As your laptop ages you probably don’t need your processors to run at 100% constantly. Mine is set to 95% and that alone gave me about a 5 degree drop in core temperature.
My old laptop, which is now my field machine, lived the first years of its life set up in my home office. It hardly ever went mobile (only when I traveled out of town). It is way past average life expectancy and still runs great at ten years old. So, heed the warnings and follow these simple suggestions and avoid these expensive and common laptop repairs in your future. You can find more information on laptop repair here.
SEO – Search Engine Optimization
SEO Louisville
There are few things more frustrating than building or paying for a website and not making it onto the first or second page of the search results. There are many reasons a website can be lost in the noise of the Internet. SEO or Search Engine Optimization is about getting your website to show up in search results. For those trying to get their business to show up it can be an expensive proposition to show up in search results in terms of not only money but time and energy, as well. To make matters worse there are hundred of ranking factors and they are not released by the search engines. One can only “guess” what they are supposed to do. Search Engine Optimization Companies study and conduct research on search engine results in an attempt to quantify what is necessary for a website to rank. Here are some basics that SEO Services have identified and agree are essential. . . .
The First Step . . . . Make A Website

First, you have to have a website. Think of your website as your primary residence on the internet. After that, you need the following (and many more) elements on that site:
Keywords: One of the primary tools that search engines utilize to determine the relevance of your website vs what the searcher is looking for are keywords. In general terms, does your website contain the vocabulary that is relevant to the topic? For example, if your website is about weight loss, the search engines might expect to see the words/terms weight loss, diet, exercise, fat, muscle, cardio, carbohydrates, goal and so on. Keyword ideas can be found from any of the numerous keyword tools available online. Avoid keyword stuffing though; look it up.
Images: The search engines want to find the best webpages. Regardless of age, people enjoy looking at pictures. Be sure you’re using images on your webpages. Also be sure you have ALT attributes on your images. That is the name of the image when hovered over by a mouse. Keep the number of images reasonable. Google is succeeding at developing a method for analyzing images better and identifying the content on the image.
Currency: It’s important to continuously add content to your website. The search engines like to see that your website is staying current and that you’re attempting to add some real value to the search engine. A dead website will eventually slip down in the rankings. Keep a schedule, be consistent and stay on top of your website content.
Backlinks: Backlinks are not “on your website” rather they point at it from other websites. Backlinks are basically a vote. But it’s not just the number of backlinks that matters; it’s also the quality of the backlinks. A link to your website from Harvard University will be given more credibility than a link from a less prestigious source. Be sure to earn backlinks by providing quality content to credible sources. Do not “place them.” If credible sources like your content they may feature it on their website.
Second….Claim Your Local Listings
Google My Business: There’s an excellent chance that Google has already found your business and created a rudimentary listing for you. To claim your listing:
→Sign into (or create) a Google account. A Google account is free; so don’t be concerned if you don’t have one. Search for your business with your city and state in the search criteria. You’ll be looking for your business with a pink balloon by it. If you see it, Google already knows your business exists.
→You will be given options to verify that the listing is yours. This is done by phone or postcard. The phone is much faster! You can then edit the listing. While you can edit the listing prior to the verification process being completed, the edits will not take effect until after the verification. ll be able to fill out the simple form online.
→Again, the listing will have to be verified. You wouldn’t want a competitor claiming or creating your listing.
Yahoo Local: Yahoo provides a similar service called Yahoo Local.
→Again, you’ll need an account with Yahoo. It’s also free. You’ll again be given the opportunity to claim an existing listing or to create a new listing.
→Either way you’ll have to wait for a verification via mail. When you receive a verification code in the mail it will give you a website address where you can verify your listing. Simply enter the code.Be sure to complete the entire listing. This includes a photo, hours, payment options, contact information, etc. You can also include information about your products and services.
Bing Places: Bing’s local listing service is called ‘Bing Places’.
→Of course, a free Microsoft account is needed.
→Search for your business. If you can find it, go through similar process to claim your listing. If you can’t find it, which is common for Bing Places, you’ll have to create a listing.
→Click the link above to visit Bing Places for Business
Third. . . .Develop Your Web-wide Presence
There are hundreds of ranking factors for appearing in search results but once you’ve accomplished the basics: you have a website, have the basic SEO elements on your website, and have claimed your local listings you need to develop your web wide presence, further. There are many small internet properties you need to have your site listed on. These are called Internet Directories. Sites like YP.com, Mojo Pages, Whitepages, Foursquare, Local.com and Manta will let you list your sites in their directory for free. Your company information should be consistent and up to date across the entire internet ecosystem.
Fourth . . . Create Your Social Media
In my opinion, you, or someone within your company should be responsible for your social media listings. No one is going to take the care in developing these that you will. The big sites you need to have a business page for are: Google+, Twitter, Facebook, Pintrest, and LinkedIn. Here you can connect with other local business and customers and interact on a local basis. You can post updates, sales, and other information about your business and start to develop online relationships locally and around the world.
Glossary of SEO Terms
It’s hard to speak any language effectively if you don’t know the relevant terminology. Over time the SEO field has developed its own unique vocabulary. With a few minutes of reading, you’ll know the language necessary to be able to speak intelligently with any SEO expert.
Alexa: You’ve probably heard of Alexa rankings. This free service measures traffic for many websites. You can see how you rank compared to your competitors or conduct other relevant research at the Alexa website.
Anchor Text: The text on a webpage that is clicked to follow a hyperlink — often underlined differentiated by color.
Authority: This is the ability of your website or web page to rank effectively with the search engines based on the perceived knowledge you or your company has in your field.
Black Hat SEO: These are SEO practices that the search engines consider to be underhanded. Each search engine has its own set of guidelines. For Google they publish a digital document called “Google Webmaster Guidelines.” If you’re outside the guidelines, it’s considered to be ‘Black Hat SEO’ and you are subject to various penalties.
Broken Links: This is simply a hyperlink on a webpage that isn’t functioning properly. In most cases, the target of the link has been removed and one clicking the hyperlink is directed to a webpage that gives a “404 error” meaning it no longer exists.
Conversion: A conversion is an impression that turns into a click.
De-Listing: The term for having your website either permanently or temporarily de-indexed from one or more directories or search engines. That is to say, removed from search engine results.
Domain Age: Many search engines and social networks consider the age of a website, page, or domain in determining relevance, trustworthiness, etc. Having an older domain is usually advantageous but not always. There are many factors in ranking of which “age of domain” is simply one. It is not unusual to see a new high quality website outrank an old, mid-quality one.
Duplicate Content: Similar to plagiarism, duplicate content is content on your website that too closely mimics content on other websites.
External Link: A link of your website that links to another website.
Impression: An impression is a unit of measurement that counts as one appearance of your website or a page on your website in search results.
Internal Link: A link to another page on the same website
Keyword: A search term or phrase you think users might type into search engines to find goods, services, or content.
Keyword Density: The frequency a specific keyword appears in web content; usually described as a percentage.
Keyword stuffing: Using a keyword on a webpage in an unnatural manner and at a frequency considered excessive by the search engines.
Landing Page: The webpage a searcher lands on when they click a title/description in search results – usually the home page or “page one” of a website.
Long-Tail Search Criteria: Typically longer, more specific search terms for a given topic, for example: “24/7 locksmith service in Chicago, ill” vs. “Chicago locksmith.”
Niche: The main subject matter of a particular website. For example, a website might be in the high-end wine or baby toy niche.
Nofollow: These are links that prevent any link authority from being passed to the link object. For example, most forum comment or blog comment links are nofollow.
Organic Search Results: These are the search results that naturally appear on search engines that are neither part of the paid or local result.
Page Rank: A logarithmic means of ranking web content.
Relevancy: The ratio of accuracy between search intention and search result.
SEO: short for “Search engine optimization” is the science and art of making a website or web page attractive to both search engines and users.
Search Criteria: The word or string of words one types into a search engine in an attempt to yield a desired search result.
SERP: Search engine results page or the list of abstracts one sees after entering search criteria into a search engine search box.
Site Map: A site map provides an alternate means for search engines to crawl and interpret a website.
User Sitemap: An intra-site map which serves as a “table of contents” to help user navigate a website.
URL: Uniform Resource Locator often referred to as simply web address. Each webpage on the internet has its own unique URL.
Call Us, Today To Discuss Your Internet Marketing and SEO
It’s not easy keeping up with all the sweeping changes in the competitive world of Search Engine Optimization. In fact, today it should not be called search engine optimization at all. It should be called “customer optimization.” The search engines such as Google, Bing and Yahoo are getting smarter all the time and they don’t allow many old SEO techniques which are called “webspam” now. You may not be aware that many methods companies used to employ for SEO may hurt your ranking status now. Today, proper SEO is all about adding quality and value on the world wide web. Google states in webmaster guidelines that you should “Make pages primarily for users, not for search engines.” This is the shift we try to help our clients understand. We want to focus on the technical aspects of your website, yes but more importantly we want to provide real value and content for your customers so you’ll become relevant in your industry, naturally.
At On-Site Louisville Computer Repair Company we’ve learned this lesson, adapted to it, and we’re ready to pass on our knowledge to you and help your website thrive in the new virtual search environment. If you need an SEO Consultant we are here to help you sift through the mounds of information and make sense of it all and boost your website’s search performance. Whether you’re interested in paid, local or organic search performance you can call us to discuss your Search Engine Optimization in Louisville, KY or anywhere so when people look for your services online — they can find YOUR Company — not just your competitors.
How To Set Up Your New Computer
 At On-Site Louisville Computer Repair Co. I often get asked to set up new computers for people. This is a good idea since there is much involved in the process. Nevertheless, there are many people that like to do things themselves, so I wrote this article for you “Do-it-yourselfers” which covers the process. Hope this helps.
At On-Site Louisville Computer Repair Co. I often get asked to set up new computers for people. This is a good idea since there is much involved in the process. Nevertheless, there are many people that like to do things themselves, so I wrote this article for you “Do-it-yourselfers” which covers the process. Hope this helps.
Get Your Files off Your Old Machine
If you have files and folders on your old machine you need to put them on a portable storage device, a flash drive, and then move them to your new machine after you set your computer up… I would leave a copy of the files on the flash drive and that is your back-up should you experience a catastrophic machine failure in the future.
Plug In, Go Through Set-up Menu and Run Your Updates:
When you turn your new computer on you will be prompted to choose settings for the computer name, time zone, language, network, updates, etc. This is very intuitive — just fill in the blanks. This is also a good time to register the computer and software. Then you are ready to run updates. Since your machine has been sitting on a warehouse or retailer’s shelf for a while you will have updates due at the time of purchase.
Uninstall Bloatware and Activate Antivirus Software Suite
Bloatware is the software that will come preloaded with your brand new laptop or desktop in the form of 30 day trials or trail subscriptions or other junk. While this software may not be harmful (debatable) most of the times they are just a waste of space. To remove simply go to Control Panel > Add/Remove> Uninstall. If your machine has a one year subscription to an antivirus suite you can activate that at this point. Otherwise you can uninstall the 30 day antivirus trial and read my article on “Five Free Antivirus Suites You Can Try for Zilch.”
Creating a System Restore Disk
You can create a restore disk in case something happens and you need to restore your computer to its factory state. Since most computers come with a recovery partition that allows you to recover your computer to factory state, making is disks is optional; however, there are circumstance where the recovery manager will not function normally, such as destruction of the partition by a virus infections, etc. Therefore many people still choose to create disks in case of emergency. To do this:
♦Go to start menu.
♦In the search bar, type “backup”.
♦Click on the “backup and Restore” option.
♦On the left side of the panel, you will see an option “create a system repair disc”.
♦Click on the option and follow the process.
Configure Power Options:
Familiarize yourself with the power settings and options available in your computer. In Windows Vista and 7 just go to start and search for “Power Options.” You can configure all your power options here including when the screen turns off, when or if the computer sleeps, what happens when you close the lid and what the power button does.
Choose Your Home Page and Make Bookmarks
When you get on the internet with Internet Explorer you probably want the page that comes up to be your favorite search engine, or your Email Login Page (which are often the same place). Most people set their homepage to Google, Yahoo, or Bing. In your browser window go to Tools>Internet Options> and then set your home page to the preferred URL. This is also a good time to visit your Bank Website, Favorite Shopping Site, and other places you visit on a regular basis and add those websites to your favorites, favorite’s toolbar, or bookmarks.
Transfer Your Files From Your Old Machine
Remember the files we pulled off your old machine earlier? Now is a good time insert your flash drive and drag old documents, photos, and music to your new computer. Plug in the flash drive and wait for it to populate “Computer” screen. Then drag a copy of your files, photos and music to the appropriate folder on your new machine and get back to computing as usual on your new computer!
Should You Buy a Tablet, Laptop, or Desktop in 2025?
With so many computing devices available today, choosing between a tablet, laptop, or desktop can feel overwhelming. Each has its advantages and drawbacks, depending on your needs. Let’s break down the pros and cons of each to help you make the best decision for your lifestyle and work habits.
Tablets: Portable and Versatile
Tablets have come a long way in the past decade. Once seen as secondary devices for media consumption, they are now more powerful than ever, capable of handling tasks that were once reserved for laptops. With advancements in attachable keyboards, stylus functionality, and cloud-based software, tablets can be a great choice for people on the go.
Pros:
- Extremely lightweight and portable, usually under a pound.
- Long battery life compared to most laptops.
- Great for casual browsing, reading, and note-taking.
- Touchscreen and stylus support for creative tasks.
- Some models, like the iPad Pro and Microsoft Surface, can be used for professional work.
Cons:
- Limited software compared to a full laptop or desktop.
- Smaller screen size can be a drawback for serious work.
- Lacks the full functionality of a desktop or powerful laptop.
If you primarily need a device for browsing, email, media consumption, or light productivity, a tablet might be a great option.
Laptops: The Best of Both Worlds?
Laptops continue to be the go-to device for students, professionals, and travelers. With a full keyboard, larger screen options, and the ability to run powerful applications, they strike a balance between portability and performance.
Pros:
- More powerful than tablets, capable of running full software suites.
- Portable yet powerful enough for work and entertainment.
- Comes with built-in keyboards, webcams, and trackpads for all-in-one functionality.
- Can connect to external monitors and accessories when needed.
Cons:
- Generally heavier and bulkier than tablets.
- Shorter battery life compared to tablets.
- Can be more expensive, especially for high-performance models.
If you need a device for work, school, gaming, or creative software like Photoshop or video editing, a laptop is a solid choice. Many professionals even use a laptop as their primary workstation by connecting it to an external monitor and accessories when at home.
Desktops: The Powerhouses
Desktops remain the most powerful and customizable option. While they lack portability, they make up for it with performance, upgradability, and a larger display experience.
Pros:
- Best performance for intensive tasks like gaming, video editing, and 3D rendering.
- Easier to upgrade and repair than laptops or tablets.
- No battery concerns – always plugged in.
- Supports large monitors for an immersive work or gaming setup.
- More secure – desktops are rarely stolen compared to laptops and tablets.
Cons:
- Not portable – you’re tied to one location.
- Requires more space for a tower, monitor, keyboard, and mouse.
- Typically uses more power than a laptop or tablet.
If you need serious computing power and don’t require mobility, a desktop is the way to go. Many professionals and gamers still prefer desktops for their superior performance and longevity.
Which One Should You Buy?
- For portability and casual use → Tablet
- For work, travel, and versatility → Laptop
- For performance, gaming, and longevity → Desktop
Technology has blurred the lines between these devices, but knowing your specific needs will help you choose wisely. Whether you’re editing videos, working remotely, or just browsing the web, there’s a perfect device out there for you!




